It’s easy to assume that compliance is something your business either has or doesn’t have. In reality, compliance is an ongoing process that must be maintained.
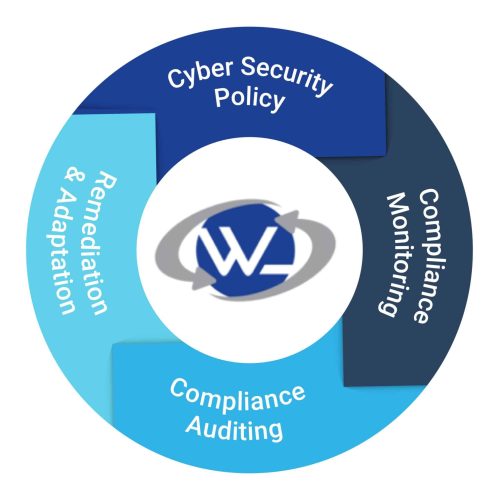
Our approach to compliance follows four key steps. It begins with establishing a clear cybersecurity policy for your organization. Once this is clarified, we move into the compliance monitoring stage. Then, periodic compliance auditing comes into play. Based on audit results, remediation and adaptation takes effect before returning to your cybersecurity policy to make necessary adjustments.
This is the starting point of organizations establishing standards for managing and protecting information technology assets. The policy generally includes protocols for security measures, risk management, and compliance with relevant laws and regulations.
Once cybersecurity policies are in place, compliance monitoring involves continuously assessing IT systems to ensure they adhere to these policies and any applicable regulatory requirements. This is a proactive process to identify and address gaps in compliance before they can be exploited by threats.
This step involves a formal review of an organization's adherence to regulatory standards and cybersecurity policies. Audits can be conducted by internal staff or external auditors. They provide a snapshot of how well the organization is meeting its compliance obligations and where improvements are needed.
Based on the outcomes of compliance audits, remediation involves taking corrective actions to resolve any issues found. This could include patching software, updating systems, training staff, or revising policies and procedures to better protect against vulnerabilities and enhance compliance.
Following remediation, organizations should revisit their cybersecurity policies. This revision is informed by the insights gained during monitoring, auditing, and remediation activities. The goal is to strengthen policies to ensure they remain effective against evolving threats and compliance requirements.
By continuously cycling through these steps, organizations can maintain a robust cybersecurity posture that adapts to new threats and compliance demands.
Wolff Logics provides comprehensive compliance services focusing on key areas such as HIPAA and PCI compliance. Our approach includes proactive risk assessments, compliance monitoring, and robust remediation strategies.
Wolff Logics begins by conducting thorough risk assessments to identify potential vulnerabilities within an organization’s IT infrastructure. We focus on ensuring that all systems comply with HIPAA regulations, which is crucial for healthcare providers to protect patient information. Our services include on-site visits, software assessments, and regular compliance reporting to maintain ongoing compliance and security.
For businesses handling credit card information, Wolff Logics offers PCI compliance services to ensure that payment data is protected according to the Payment Card Industry Data Security Standard (PCI DSS). This includes PCI-approved scans and mitigation services to detect and address security vulnerabilities, thus helping businesses avoid penalties and maintain trust with customers.
These services are part of Wolff Logics’ broader managed IT services, which also include 24/7 monitoring of systems and data, real-time employee monitoring, and other cybersecurity measures to prevent data breaches and ensure continuous operational compliance.
Full-Disk and File Encryption ensure that none of your sensitive data falls into the wrong hands.
Multiple levels of protection, all from a single interface.
Your clients’ financial security is one of their top concerns. Shouldn’t it be yours, too?
Keep employee mobile devices secure.
Major cyber attacks occur every month. Unfortunately, it’s not a matter of if it happens to you, but when.
Having great backup and disaster recovery procedures is a good start, but it shouldn’t be the only tool in your arsenal. After all, you have home insurance, but that doesn’t mean you leave your front door unlocked.
Stop hackers, SPAM, malware, and other threats in their tracks with the right level of security from Wolff Logics.
Or Call Us Today 855-222-5248

Foolproof data security. Peace of mind for you, protection for your clients.
Data breach, loss, and theft no longer have to be a problem. Wolff Logics offers several layers of encryption to stop cybercrime in its tracks, no matter where the threat is coming from.
Full Disk Encryption puts your data under lock and key as soon as its created and unlocks it automatically from whatever device you choose, no passwords necessary. Even if someone manages to hack into your network or take your hard drive, your data stays locked up and out of reach.
And if your entire laptop is stolen, strong, password-protected file encryption ensures that no one will be able to access sensitive data unless they are authorized. Your files remain encrypted no matter who you share it with, so you don’t have to worry about your clients’ data falling into the wrong hands.
We can also protect any exchange of information with our Encrypted Email service. Now, you don’t have to be worried about confidential messages being intercepted when they leave the security of your network. Whether you want your process to remain seamless or you want the added reassurance of password-protecting your emails, Wolff Logics can set up a secure system that you and your clients will appreciate.
Your clients’ sensitive information is too valuable not to be protected.
You can’t fix the problem if you don’t know it exists.
When dealing with personal information or HIPAA compliance, data security is non-negotiable. But you can’t fix the problems if you don’t know that they’re there.
That’s where Wolff Logics comes in.
With our security risk assessments, we can uncover the holes in your network security so that you remain a safe, secure repository of your clients’ and patients’ sensitive information. You remain HIPAA-compliant. You remain trustworthy.
Full-service firewall with one simple install.
The threats to your security don’t just come from one source. Hackers, malware, SPAM, and other intrusions can all derail your patient confidentiality.
With the UTM service from Wolff Logics, you can protect against all these threats and more from a single interface. Just one software install, and you’ve got an entire arsenal at your fingertips: an advanced firewall and threat protection, anti-malware, SPAM filters, and unlimited VPN capabilities, all from one dashboard.
Your IT network is made up of a host of components: email, websites, data storage, networks, and more. Using a single threat management system is the best way to ensure that there are no weaknesses or holes in your protection. A UTM makes it easier for you to monitor the threats and deploy fixes when the need arises.


You don’t have to sacrifice security for convenience.
The Payment Card Industry’s Data Security Standard was created to make sure that businesses just like yours have systems in place to protect their customers’ financial information.
Failing to meet these standards doesn’t just mean that your clients no longer trust you, it could also mean losing the ability to accept credit card payments.
Can your business survive on cash and checks alone?
Wolff Logics PCI-approved scans and mitigation services make sure that you stay PCI-compliant so you can stay in business. Our assessment services uncover any threats within your cardholder data environment (from your software to your POS system) and our remediation services both document and prioritize the issues discovered so we can implement our plan of action. And an ASV-certified scan is just a click away
As mobile devices become more ubiquitous in the workplace, mobile security becomes even more important. A recent survey showed that checking smartphones first thing in the morning (within 30 minutes of waking) is now a common practice.
But many employers don’t think of the security risks involved with equipping their employees with mobile devices. With an enterprise mobility management (EMM) software, you can still get the same level of on-the-go communication with your employees without sacrificing security.
With enterprise mobility management, you can:
Keeping an eye on your employees no matter where they are helps increase productivity and collaboration. With EMM, you don’t have to sacrifice security for ease of use.

Don’t take a casual approach to your data security. After all, backups and data recovery won’t protect you against malware or hackers.
At Wolff Logics, we take your security seriously. From email to mobile devices, our solutions will lock up your data so you and your clients can rest at ease.
Contact Wolff Logics to get started today.

Failing PCI compliance can result in substantial fines, ranging from $5,000 to $100,000. Typically, penalties are determined based on the number of customers or transactions affected by the non-compliance. Therefore, it’s best to always maintain strict compliance
HIPAA applies to health plans, health care clearinghouses, and health care providers conducting transactions electronically (such as billing a health plan).
Every business is susceptible to cyber attacks. What separates attacks that cause substantial damage from businesses that walk away from them unscathed are the security services they had in place beforehand. Oftentimes, businesses are not aware of the security complexities required for protection from today’s cybercriminals. This is where we can help.
